Crypto security analysts are warning of a renewed surge in address poisoning scams after two recent incidents resulted in combined losses exceeding $62 million, underscoring persistent risks for blockchain users.
What Is Address Poisoning and How Victims Lose Funds
Address poisoning is a tactic where attackers send tiny “dust” transactions from wallet addresses designed to closely resemble legitimate ones. These malicious addresses often share the same starting and ending characters as trusted addresses already stored in a victim’s transaction history. When users later copy an address from their history, they may unknowingly send funds to the attacker instead.
According to blockchain security firm Scam Sniffer, one victim lost $12.2 million in January after copying a poisoned address, following a similar $50 million loss recorded in December.
Signature Phishing Losses Also Surge
Scam Sniffer also reported a sharp rise in signature phishing attacks, where users are tricked into approving malicious transactions such as unlimited token allowances. In January alone, $6.27 million was stolen from 4,741 victims, marking a 207% increase from the previous month. Notably, just two wallets were responsible for roughly 65% of those losses.
Ethereum Network Changes Linked to Rising Attacks
Security researchers suggest that Ethereum’s Fusaka upgrade has reduced transaction costs, making dust attacks significantly cheaper to execute. Recent data indicates that tiny stablecoin transfers now account for a meaningful share of daily Ethereum activity, signaling widespread poisoning attempts.
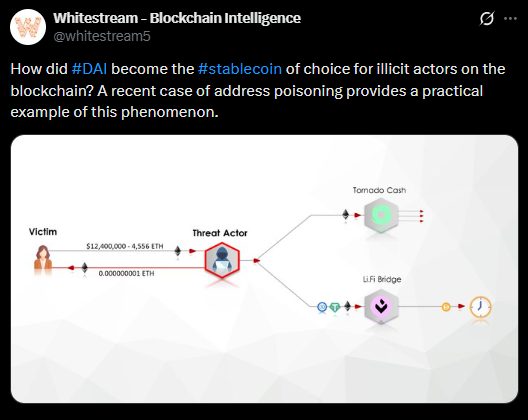
Analysts warn that without improved user vigilance and wallet safeguards, address poisoning remains one of the most effective methods for large-scale crypto theft.
Disclaimer
This content is for informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency trading involves risk and may result in financial loss.

