The plugin ecosystem of the open-source AI agent framework OpenClaw is facing a significant security threat after hundreds of malicious plugins were discovered, according to a recent cybersecurity report.
Hundreds of Malicious AI Plugins Identified
Blockchain security firm SlowMist revealed that attackers have been actively uploading poisoned plugins, known as “skills,” to OpenClaw’s official plugin hub, ClawHub. The firm identified 472 AI skills containing malicious code, triggering high-severity alerts through its Web3 threat intelligence system. The issue is attributed to weak or absent review processes, allowing harmful plugins to be distributed to unsuspecting users.
How the Supply Chain Attack Works
The malicious skills are disguised as legitimate dependency installation packages. Once installed, they execute hidden commands that activate backdoors on user devices. These backdoors, often encoded using Base64 techniques, can harvest sensitive data such as passwords, private files, and system information.
Coordinated Infrastructure Behind the Attacks
Most of the poisoned plugins trace back to a single malicious domain and IP address linked to known exploit infrastructure. The reuse of domains, IPs, and identical attack patterns strongly suggests an organized and coordinated operation rather than isolated incidents.
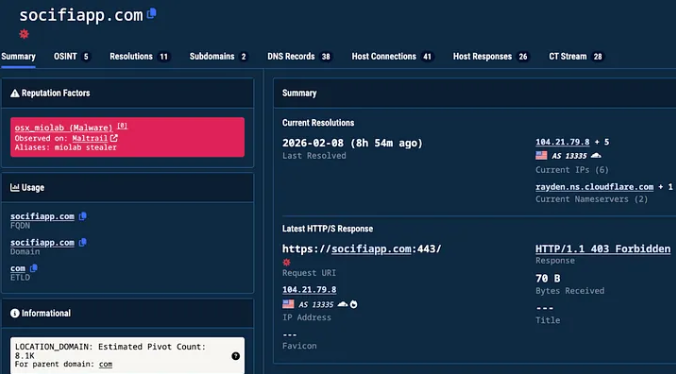
The infected plugins frequently use names related to cryptocurrency, financial automation, and trading tools—categories more likely to attract crypto investors and lower their security vigilance.
SlowMist advises users to carefully audit plugin documentation, avoid executing copied installation commands blindly, and be cautious of any AI skill requesting system passwords or elevated permissions.
Disclaimer
This content is for informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency trading involves risk and may result in financial loss.

