Cetus Protocol, a well-known liquidity platform on the Sui blockchain, has fallen victim to a massive security breach, with over $150 million in assets reportedly stolen, according to on-chain data shared by BlockBeats. This exploit marks one of the most serious DeFi breaches on the Sui network to date.
“Hackers have drained multiple liquidity pools, exposing vulnerabilities in the protocol’s smart contracts,” said a cybersecurity source familiar with the matter.
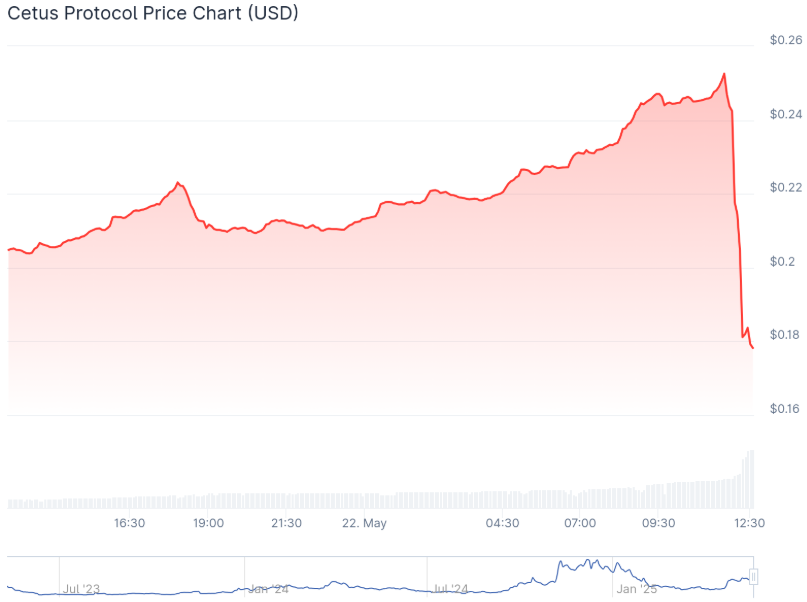
On-Chain Data Confirms Widespread Drainage
Blockchain forensics tools confirm abnormal activity across key liquidity pools on Cetus. Massive token outflows were traced to unauthorized wallet addresses, suggesting that sophisticated attackers exploited smart contract flaws or compromised private keys.
“The speed and precision of the attack suggest a coordinated effort,” noted a DeFi analytics firm.
Key trading pairs such as CETUS/SUI, USDC/SUI, and others were hit the hardest, resulting in major slippage and halted trades.
CETUS Token Plunges as Panic Sets In
The CETUS token crashed by more than 60% within hours, as panic spread among holders. Many users rushed to exit their positions, further accelerating the price drop and increasing volatility across the platform.
“Liquidity vanished in minutes, and slippage became unbearable,” commented a long-time Cetus user.
Market Impact
LOFI: Dropped over 70%
CETUS Token: The native token of Cetus Protocol experienced a sharp decline, dropping over 40% in value shortly after the exploit.
Sui Ecosystem Tokens: Other tokens within the Sui ecosystem also suffered significant losses:
HIPPO: Down over 17%
WET: Plummeted over 75%
Cetus Team Responds: Emergency Measures Underway
The Cetus Protocol team has acknowledged the breach, confirming that emergency steps are being taken, including:
- Pausing all smart contract interactions
- Working with the Sui Foundation and external auditors
- Advising users to revoke approvals immediately
“We are actively investigating the exploit and working to contain the damage,” said the team in an official statement on X (formerly Twitter).
DeFi Security in Question Once Again
This attack has raised new concerns about DeFi security practices, especially on emerging networks like Sui. Despite the chain’s advanced architecture, Cetus’ breach proves that protocol-level security is paramount.
“This is a wake-up call for the entire ecosystem to enforce stricter smart contract auditing and monitoring,” stated a blockchain security analyst.
Trust in Sui DeFi Ecosystem Shaken
The $150 million Cetus Protocol hack is a major blow to DeFi confidence on the Sui network. Until security mechanisms improve across the board, users and developers may hesitate to engage with emerging DeFi platforms — no matter how innovative they appear.

